Table of Contents
The landscape of cybersecurity is changing fast with cyber threats looming everywhere in the digital space making penetration testing a key element to be considered in software development. Penetration testing, also called ethical hacking, serves as an important tool for mitigating these cyber risks by actively identifying vulnerabilities and possible exploits within software systems. Digital transformation has brought a complex terrain for organizations that necessitates increased security measures.
According to the 2023 survey, 85% of data breaches are caused by human error, misconfiguration or vulnerabilities that could have been found through penetration testing. These breaches come at a significant cost, with the average data breach costing enterprises $4.24 million globally in the year 2023, according to Statista. Additionally, there has been a spike in the number of cyber-attacks witnessed with McAfee reporting that cloud servers encountered 6 times as many attacks in 2020 alone.
Given this heightened threat landscape, regulatory institutions have adopted stringent compliance standards which prescribe periodic security assessments and vulnerability tests. Health care finance and technology sectors among others are regulated industries where such processes must be followed.
Penetration testing is an essential part of security for software development. It helps organizations find out and correct their weaknesses so that they cannot be used against them by malicious hackers. It is because of this that penetration testing does not act as only a reactive self-defence system but also functions. As one of the major strategic investments in addressing challenges associated with the long-term vulnerability control and stability of software applications in our ever-changing world today.
What is Penetration Testing: Definition and Purpose
Penetration testing is frequently alluded to as pen testing or moral hacking. However, it is an online protection practice intended to assess the security of PC frameworks, organizations, and applications. The basic role of a dynamic cone penetration test is to recognize and take advantage of weaknesses inside an association’s IT foundation, very much like a malevolent assailant would.
During a penetration test, prepared security experts, known as penetration testers or ethical hackers. Moreover, to simulate real-world cyber attacks to uncover weaknesses that could be exploited by malicious actors. These attacks might include different procedures, including network checking, social designing, and double-dealing of programming weaknesses.
A definitive objective of penetration testing isn’t just to distinguish weaknesses yet in addition to survey the viability of existing security controls and measures. By revealing shortcomings and potential passage focuses, network scanning, social engineering, and exploitation of software vulnerabilities.
Penetration testing, in general, is a preventative safety measure that aids organizations in identifying and fixing vulnerabilities before malevolent actors may exploit them. However, It provides valuable insights into the feasibility of current safety initiatives and enables groups to concentrate on them. It also permits resources to truly solve fundamental security concerns.
Why Penetration Testing is Crucial in Software Development?
Penetration testing, an integral component of cybersecurity protocols, fills in as a proactive safeguard system in software development. However, by simulating real-world cyber attacks, automated penetration testing empowers organizations to recognize and address vulnerabilities before they can be taken advantage of by malicious actors. How about we dig into the key motivations behind why penetration testing is critical in software development:
Penetration testing holds critical significance in software development for a few compelling reasons:
1. Identifying Vulnerabilities
Penetration testing recognizes possible vulnerabilities and security weaknesses inside software applications. By recreating real-world cyber attacks, penetration testers uncover hidden flaws that could be exploited by malicious actors.
2. Proactive Risk Management
Conducting penetration tests during the software development lifecycle permits organizations to proactively oversee risks. By identifying vulnerabilities early on, hire software developers can execute fundamental security measures to relieve expected threats before they grow into huge security episodes.
3. Ensuring Application Security
Penetration testing guarantees the security for software development by approving the viability of existing security controls and measures. However, It assists organizations with surveying the flexibility of their applications against different assault vectors and situations. However, it includes network interruptions, information breaks, and unapproved access attempts.
4. Compliance Requirements
Numerous regulatory systems and industry norms command customary penetration testing as a feature of compliance requirements. However, sticking to these norms assists organizations with showing their obligation to security and compliance. In this manner staying away from regulatory punishments and legitimate liabilities.
5. Enhancing Customer Trust
Putting resources into penetration testing shows a guarantee of security and customer trust. By proactively tending to security vulnerabilities, organizations impart trust in their customers and partners. Consoling them that their delicate information is safeguarded against possible threats.
6. Preventing Financial Losses
Penetration testing helps prevent financial losses related to information breaks, framework personal time, and reputational harm. By identifying and curing security vulnerabilities from the get-go, organizations limit the risk of costly security episodes that could antagonistically affect their primary concern.
7. Improving Software Quality
Penetration testing adds to the general quality of software items by revealing imperfections and vulnerabilities that might think twice about trustworthiness and dependability. By tending to security issues during the development phase, organizations can convey safer and stronger software answers for their customers.
The cost of custom software development is important since it distinguishes vulnerabilities, proactively oversees risks, ensures compliance with regulatory requirements, enhances customer trust, prevents financial losses, and improves the overall quality of software applications. By incorporating penetration testing into their development processes, organizations can fortify their security act and safeguard against advancing cyber threats.
How Penetration Testing Safeguards Against Security Threats?
Penetration testing, a cornerstone of cybersecurity practices, assumes a crucial part in safeguarding against security threats in software development. By simulating real-world attack scenarios, penetration testing enables organizations to recognize and address vulnerabilities before they can be taken advantage of by malicious entertainers. We should investigate how penetration testing safeguards against security threats:
1. Identifying Vulnerabilities
Penetration testing involves systematically probing software frameworks, organizations, and applications for weaknesses and vulnerabilities. By uncovering potential section points and security flaws, penetration testing assists organizations with understanding their gamble openness and focus on remediation efforts.
Secure Your Systems Now!
2. Assessing Security Controls
Penetration testing assesses the adequacy of existing security controls and measures conveyed within software applications. Software penetration testing surveys the versatility of firewalls, intrusion detection frameworks, access controls, and other security mechanisms to determine their capacity to endure attacks and protect against unauthorized access.
3. Exploiting Weaknesses Ethically
Unlike malicious hackers, penetration analyzers exploit vulnerabilities ethically and with authorization from the association. By mimicking the tactics and techniques utilized by real attackers, penetration testing gives important insights into the association’s security stance and readiness to protect against cyber threats.
4. Mitigating Risks
By identifying vulnerabilities and weaknesses right off the bat in the software development lifecycle, penetration testing enables organizations to effectively mitigate risks. It permits engineers and security groups to address security issues quickly. Reducing the probability of data breaks, financial losses, and reputational damage.
5. Enhancing Incident Response Preparedness
This testing assists organizations with enhancing their incident response preparedness by simulating different attack scenarios and evaluating the adequacy of response methodology. By identifying holes in incident detection and response capabilities, penetration testing enables organizations to refine their incident response designs and minimize the effect of security incidents.
6. Ensuring Regulatory Compliance
Numerous regulatory systems and industry guidelines expect organizations to lead penetration testing as a feature of their compliance efforts. By demonstrating proactive security measures and adherence to regulatory requirements are considered to be software development best practices, penetration testing assists organizations with avoiding non-compliance penalties and legal liabilities.
7. Building Trust and Confidence
By proactively identifying and addressing security vulnerabilities, penetration testing instills trust and confidence among stakeholders, including clients, accomplices, and regulatory bodies. Automated penetration testing exhibits the association’s obligation to safeguard sensitive data and protect against cyber threats, enhancing its reputation and credibility in the commercial center.
This testing fills in as a proactive security measure that safeguards against security threats by identifying vulnerabilities. However, assessing security controls, mitigating risks, and enhancing incident response preparedness. Ensuring regulatory compliance, and building trust and confidence among stakeholders. Moreover, by integrating penetration testing into their cybersecurity methodologies, organizations. Subsequently, it can strengthen their safeguards and mitigate the effect of potential security incidents.
Types of Penetration Testing Methods and Approaches
Penetration testing includes different methods and approaches tailored to address specific security concerns and goals. Probably the most widely recognized kinds of dynamic cone penetration test methods and approaches include:
1. Black Box Testing
In black box testing, otherwise called external testing, the penetration analyzer has restricted information on the internal functions and architecture of the framework being tried. However, this approach recreates the point of view of an external attacker endeavoring to acquire unapproved access to the objective framework or network.
2. White Box Testing
White box testing additionally alluded to as internal testing, concedes the penetration analyzer full access to the source code, architecture, and internal components of the framework being tried. This approach considers a comprehensive assessment of vulnerabilities and weaknesses according to an insider’s viewpoint.
3. Gray Box Testing
Gray box testing consolidates components of both black box and white box testing approaches. However, the penetration analyzer has partial information on the internal activities of the framework, for example, access credentials or network diagrams, while as yet reproducing the point of view of an external attacker.
4. Network Penetration Testing
Network penetration testing centers around assessing the security of network foundations, including switches, switches, firewalls, and servers. Penetration analyzers endeavor to exploit vulnerabilities in network configurations and conventions to acquire unapproved access or upset network operations.
5. Web Application Penetration Testing
Web application penetration testing includes assessing the security of web-based applications, websites, and APIs. Penetration analyzers survey vulnerabilities, for example, SQL injection, cross-site scripting (XSS), and authentication bypass to distinguish possible roads for exploitation.
6. Wireless Penetration Testing
Wireless penetration testing inspects the security of wireless networks, including Wi-Fi and Bluetooth networks. Penetration analyzers evaluate encryption conventions, access controls, and network configurations to distinguish vulnerabilities that could be exploited by unapproved clients.
7. Social Engineering Testing
Social engineering testing includes exploiting human brain science and conduct to acquire unapproved access to sensitive data or frameworks. Penetration analyzers utilize different techniques, for example, phishing emails, pretexting, and impersonation, to manipulate individuals into disclosing confidential data or performing unapproved activities.
8. Physical Penetration Testing
Physical penetration testing assesses the physical security controls and measures set up to safeguard sensitive assets and facilities. Penetration testers use various techniques to bypass physical barriers. For example, locks, access control frameworks, and surveillance cameras, to acquire unapproved sections to limited regions.
These are only a couple of instances of the different scopes of penetration testing methods and approaches accessible to custom software development services looking to evaluate and improve their cybersecurity guards. Contingent upon the specific requirements and targets of the testing engagement, organizations might utilize at least one of these methods to effectively distinguish and remediate vulnerabilities.
The Process of Conducting Penetration Testing: Step-by-Step Guide
Conducting penetration testing includes a deliberate process pointed toward distinguishing and addressing security vulnerabilities inside an association’s frameworks, networks, and applications. The following is a step-by-step guide outlining the process of conducting penetration testing:
1. Define Scope and Objectives
Start by characterizing the scope and objectives of the penetration testing commitment. Decide the frameworks, networks, and applications to be tried, as well as the specific objectives and objectives of the testing exertion.
2. Gather Information
Conduct reconnaissance and information gathering to gather important information about the target environment. This might incorporate recognizing network foundations, mapping out application engineering, and gathering information about potential attack vectors.
3. Threat Modeling
Perform threat modeling to recognize potential threats and attack vectors that could be utilized by malicious actors. Analyze the target environment according to an attacker’s point of view to prioritize potential dangers and vulnerabilities.
4. Vulnerability Analysis
Conduct vulnerability analysis to recognize known vulnerabilities and weaknesses inside the target environment. Utilize computerized examining apparatuses, manual testing strategies, and restrictive contents to distinguish security imperfections and misconfigurations.
5. Exploitation
Once vulnerabilities have been identified, attempt to exploit them to gain unauthorized access or escalate privileges within the target environment. Utilize penetration testing apparatuses and procedures to exploit identified vulnerabilities and simulate real-world attack scenarios.
6. Post-Exploitation
In the event of successful exploitation, perform post-exploitation exercises to additionally survey the effect of compromised frameworks and networks. Record any sensitive information, compromised credentials or unapproved access during the testing process.
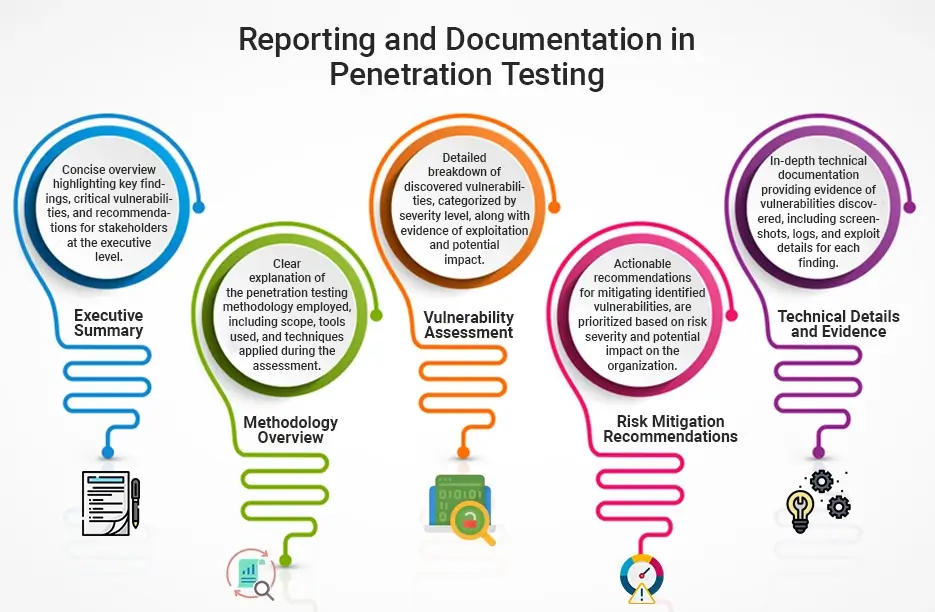
7. Documentation and Reporting
Record all discoveries, perceptions, and suggestions in a far-reaching penetration testing report. Incorporate insights concerning identified vulnerabilities, exploited weaknesses, and recommended remediation actions. Give clear and noteworthy direction to assist partners with addressing security issues and mitigating gambles.
8. Remediation and Follow-Up
Work intimately with partners to prioritize and address identified security vulnerabilities and weaknesses. However, teaming up with IT groups, designers, and framework overseers to execute remediation gauges and reinforce security controls inside the target environment. Conduct follow-up testing as needed to validate the effectiveness of remediation efforts.
9. Continuous Improvement
Penetration testing ought to be seen as an iterative process focused on continuous improvement. Moreover, consistently survey and update security strategies, methods, and controls in light of illustrations gained from penetration testing commitment. Incorporate feedback and insights acquired from testing efforts to improve general security posture and versatility.
By following this step-by-step guide, associations can conduct penetration testing to recognize and mitigate security gambles, reinforce their cybersecurity defenses with artificial intelligence in software development and safeguard against potential threats and attacks.
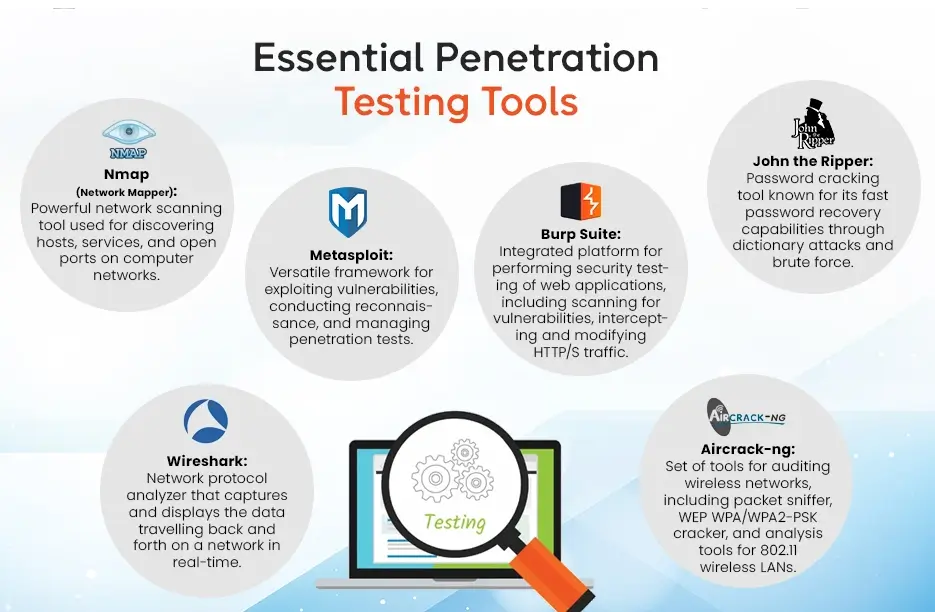
Tools and Technologies Used in Penetration Testing
Penetration testing, a critical part of cybersecurity, depends on different tools and technologies. However, to assess the security stance of systems, networks, and applications. The following are a few generally involved tools and technologies in penetration testing:
1. Vulnerability Scanners
Automated tools like Nessus, OpenVAS, and Qualys Vulnerability Management are utilized to check networks and systems for known vulnerabilities. However, these tools recognize security shortcomings in working systems, applications, and network gadgets by contrasting them against data sets of known vulnerabilities.
2. Exploitation Frameworks
Exploitation frameworks like Metasploit and Cobalt Hit furnish penetration analyzers with an exhaustive set of tools and exploits to simulate real-world attacks. These frameworks automate the method involved with taking advantage of distinguished vulnerabilities and acquiring unapproved admittance to target systems.
3. Network Scanners
Network checking tools like Nmap and Masscan are utilized to find has, administrations, and open ports inside target networks. These tools give important data about network geography, gadget fingerprinting, and potential assault vectors.
4. Password Cracking Tools
Password cracking tools like John the Ripper, Hashcat, and Hydra are utilized to recuperate or break passwords through animal power attacks, word reference attacks, or rainbow table attacks. These tools assist penetration analyzers with assessing the strength of password strategies and recognising powerless or effectively guessable passwords.
5. Web Application Scanners
Web application scanners like Burp Suite, OWASP ZAP, and Acunetix are explicitly intended to distinguish security vulnerabilities in web applications and APIs. These tools automate the method involved with creeping, testing, and investigating web applications for normal vulnerabilities. For example, SQL injection, cross-site scripting (XSS), and uncertain confirmation systems.
6. Wireless Penetration Testing Tools
Wireless penetration testing tools, for example, Aircrack-ng and Kismet are utilized to assess the security of wireless networks, including Wi-Fi and Bluetooth networks. These tools empower custom software development companies in usa to sniff network traffic, catch handshakes, and take advantage of vulnerabilities in wireless conventions.
7. Social Engineering Toolkit (SET)
The Social Engineering Toolkit (SET) is a structure that permits penetration analyzers to recreate social engineering attacks. For example, phishing, stick phishing, and qualification reaping. SET gives a scope of tools and methods to control the human way of behaving and take advantage of mental vulnerabilities.
8. Forensic Analysis Tools
Forensic analysis tools like Post-mortem and The Investigator Unit are utilized to examine security episodes, dissect computerized proof, and recuperate erased records. These tools assist penetration analyzers with social affairs forensic information, remake assault timelines, and distinguish marks of give and take (IOCs) during post-occurrence analysis.
9. Traffic Analysis Tools
Traffic analysis tools like Wireshark and tcpdump are utilized to catch and examine network traffic in real-time. These tools with software penetration testing give profound parcel assessment capacities, permitting penetration analyzers to investigate network conventions, recognize abnormalities, and distinguish potential security dangers.
10. Custom Scripts and Exploits
Penetration testers often develop custom scripts and exploits tailored to specific testing scenarios and objectives. These scripts influence programming dialects like Python, PowerShell, and Ruby to automate tasks, exploit vulnerabilities, and lead complex attacks.
By utilizing these tools and technologies, penetration analyzers can distinguish, exploit, and remediate security vulnerabilities inside target conditions. Assisting associations with fortifying their cybersecurity safeguards and mitigating expected chances.
Benefits of Regular Penetration Testing in Software Development
Regular penetration testing assumes an urgent part in software development by giving a few advantages to organizations, including:
1. Identifying Vulnerabilities
Penetration testing recognizes security vulnerabilities and shortcomings inside software applications, organizations, and systems. By mimicking real-world attack scenarios, penetration analyzers uncover potential passage focuses that could be taken advantage of by malicious actors to think twice about data or disrupt operations.
2. Assessing Security Controls
Penetration testing assesses the viability of existing security controls and measures carried out inside the software development climate. By assessing the versatility of security instruments like firewalls, intrusion detection systems (IDS), and access controls. Organizations can distinguish holes and shortcomings that require remediation.
3. Mitigating Risks
By proactively identifying and tending to security vulnerabilities, penetration testing mitigates the risks related to potential cyber threats and attacks. Healthcare digital transformation companies can focus on and remediate recognized vulnerabilities to decrease the probability of security incidents and limit the impact of likely breaches on business operations and notoriety.
4. Ensuring Regulatory Compliance
Penetration testing assists organizations exhibit compliance with regulatory necessities and industry standards administering data security and protection. Numerous regulatory structures, for example, the Payment Card Industry Data Security Standard (PCI DSS) and the Health Insurance Portability and Accountability Act (HIPAA), order regular security testing, including penetration testing, to defend sensitive data and safeguard customer protection.
5. Enhancing Incident Response Preparedness
Penetration testing upgrades incident response preparedness by giving organizations bits of knowledge about potential attack vectors and exploitation techniques utilized by danger actors. By mimicking cyber attacks, organizations can assess their incident response abilities, train the workforce to answer security incidents and execute proactive measures to alleviate the impact of breaches.
6. Improving Security Awareness
Penetration testing brings issues to light among partners, including software engineers, framework heads, and leaders, about the significance of cybersecurity and the potential risks presented by security vulnerabilities. By highlighting the requirement for robust security measures and best practices, penetration testing encourages a culture of security awareness and vigilance inside the association.
7. Protecting Customer Trust
Regular penetration testing safeguards customer trust and certainty by exhibiting a guarantee to safeguard sensitive data and protect against cyber threats. By putting resources into proactive security testing and risk mitigation measures, organizations can console customers and partners that their data is dealt with safely and dependably.
Regular penetration testing in software development is fundamental for identifying and tending to security vulnerabilities, assessing the adequacy of security controls, mitigating risks, ensuring regulatory compliance, enhancing incident response preparedness, improving security awareness, and protecting customer trust. By incorporating penetration testing into the software development lifecycle, organizations can strengthen their cybersecurity defenses and mitigate the evolving threats posed by cybercriminals.
Challenges and Limitations of Penetration Testing
Penetration testing, while an important device for assessing and improving cybersecurity posture, likewise presents certain challenges and limitations that organizations should consider:
1. Resource Intensive
Penetration testing requires huge resources, including time, expertise, and innovation. Organizations might battle to apportion adequate resources to direct careful and successful penetration tests, particularly for complex systems and environments.
2. Scope Limitations
Penetration testing is limited by the scope defined for the commitment. Testing may just cover explicit systems, organizations, or applications, leaving different regions powerless against assault. Inadequate scope definition can bring about disregarded vulnerabilities and holes in security inclusion.
3. False Positives and Negatives
Penetration testing can deliver false positives, where non-existent vulnerabilities are incorrectly distinguished, or false negatives, where real vulnerabilities are missed. Interpreting test results precisely and distinguishing between genuine security issues and false cautions can be challenging for organizations.
4. Limited Testing Frequency
Organizations might direct penetration testing infrequently, resulting in obsolete evaluations of security posture. Standard testing is fundamental for identifying emerging threats and vulnerabilities, however, resource constraints and competing needs might restrict the frequency of testing endeavors.
5. Complexity of Modern Systems
Modern IT environments are increasingly complex, featuring interconnected systems, cloud infrastructure, and cell phones. Penetration testing might battle to evaluate the security of these complex environments, leading to incomplete or inaccurate gamble appraisals.
6. Technical Expertise Required For Penetration Testing
Penetration testing requires specific technical expertise and abilities in cybersecurity, networking, and system administration. Custom software development for startups might lack in-house talent or battle to find qualified outside advisors equipped for conducting exhaustive and compelling penetration tests.
Regardless of these challenges and limitations, penetration testing remains a significant part of a complete cybersecurity strategy, helping organizations identify and mitigate security risks, strengthen defenses, and safeguard against evolving threats. By understanding and addressing these challenges, organizations can boost the adequacy of their testing initiatives and upgrade generally speaking security posture.
Best Practices for Effective Penetration Testing Implementation
Effective penetration testing execution expects adherence to best practices to guarantee exhaustive and significant appraisals of security posture. Here are key prescribed procedures for leading this testing:
1. Define Clear Objectives
Establish clear and quantifiable objectives for the penetration testing engagement, including objectives, scope, and wanted results. Define the frameworks, networks, and applications to be tried, as well as the particular security controls and situations to be assessed.
2. Engage Skilled Penetration Testing Professionals
Utilize experienced and qualified penetration analyzers with skills in cybersecurity, network infrastructure, and application security. Custom software development outsourcing companies guarantee that analyzers have significant affirmations and certifications, like Certified Ethical Hacker (CEH) or Offensive Security Certified Professional (OSCP), to direct comprehensive and effective tests.
3. Follow Rules of Engagement
Establish rules of engagement (ROE) that frame the degree, system, and constraints of the penetration testing engagement. Define OK testing techniques, targets, and periods, as well as any legitimate and consistent contemplations, to guarantee dependable and ethical testing rehearses.
4. Perform Comprehensive Reconnaissance
Direct careful reconnaissance and data social affairs to distinguish potential attack vectors, vulnerabilities, and weaknesses inside the objective climate. Healthcare digital transformation companies can investigate openly accessible data, network infrastructure, and application architecture to illuminate the testing approach and focus on regions for appraisal.
5. Utilize a Variety of Testing Techniques
Utilize a variety of testing techniques, including black-box, white-box, and grey-box testing methodologies, to mimic certifiable attack situations and reveal stowed-away vulnerabilities. Consolidate automated scanning tools, manual testing techniques, and social engineering tactics to survey various layers of security controls effectively.
Measuring the Success of Penetration Testing: Metrics and Key Performance Indicators (KPIs)
Measuring the progress of penetration testing requires the foundation of applicable metrics and key performance indicators (KPIs) to assess the adequacy, effect, and benefit of testing endeavors. Here are key metrics and KPIs to consider while assessing the progress of penetration testing initiatives:
1. Vulnerability Detection Rate
Measure the percentage of vulnerabilities identified during penetration testing services solutions contrasted with the total number of vulnerabilities present in the target environment. A higher detection rate demonstrates exhaustive testing inclusion and powerful recognizable proof of security weaknesses.
2. Critical and High-Risk Vulnerabilities
Track the number and severity of critical and high-risk vulnerabilities identified during penetration testing. Center around addressing these vulnerabilities quickly to mitigate the highest-priority security risks and lessen the likelihood of exploitation by threat actors.
3. False Positive Rate
Monitor the rate of false positives generated during penetration testing, where non-existent vulnerabilities are erroneously identified as security risks. A lower false positive rate demonstrates more accurate and reliable test results, diminishing the time and exertion expected for approval and remediation.
4. Remediation Timeframe
Measure the time taken to remediate identified vulnerabilities and security issues following penetration testing. Assess the proficiency and responsiveness of the association’s remediation processes, going for the gold of security risks to minimize exposure and potential effects.
5. Risk Reduction Percentage
Ascertain the percentage reduction in generally speaking security risk following penetration testing and ensuing remediation endeavors. Analyze pre-test and post-test risk assessments to gauge the viability of security controls and risk mitigation strategies executed in response to test discoveries.
6. Incident Response Preparedness
Assess the association’s incident response preparedness and adequacy in tending to security incidents identified during penetration testing. Enterprise software development companies can assess the timeliness and adequacy of response moves initiated to contain, mitigate, and recuperate from reproduced cyber assaults and security breaks.
By monitoring and measuring these key metrics and KPIs, organizations can assess the achievement and effect of these testing initiatives, drive continuous improvement in cybersecurity practices, and upgrade by and large resilience against evolving cyber threats and vulnerabilities.
Conclusion: Leveraging Penetration Testing for Enhanced Security
Leveraging penetration testing as a critical part of cybersecurity strategy can essentially improve security posture and resilience against cyber threats. By deliberately assessing and identifying vulnerabilities, weaknesses, and security holes within IT infrastructure, applications, and networks, organizations can proactively mitigate risks, strengthen defenses, and safeguard sensitive data and resources from potential exploitation and split the difference.
It fills in as a significant tool for reenacting genuine world cyber assaults, empowering organizations to identify and prioritize security vulnerabilities, assess the viability of existing security controls, and approve incident response capabilities. Through comprehensive testing methodologies, custom software development consulting gain noteworthy bits of knowledge into their security posture, permitting them to settle on informed choices, allot assets successfully, and execute targeted remediation strategies to address identified risks and threats.
All in all, penetration testing represents a cornerstone of successful cybersecurity administration, giving organizations the bits of knowledge, tools, and capabilities expected to identify, assess, and mitigate security risks comprehensively. By coordinating penetration testing into more extensive risk-the-board practices and security initiatives, organizations can strengthen their cyber defenses, upgrade functional resilience, and maintain trust and confidence in their ability to shield against cyber threats in an undeniably interconnected and dynamic threat scene.
Frequently Asked Questions (FAQs) About Penetration Testing
1. What is Penetration Testing?
This testing is also called pen testing, is a cybersecurity practice that includes recreating genuine world cyber assaults on frameworks, networks, and applications to identify security vulnerabilities, weaknesses, and potential entry points that could be exploited by threat actors. The objective of this testing is to assess the viability of security controls, approve the association’s security posture, and identify opportunities for further developing defenses and mitigating risks.
2. Why is Penetration Testing Important?
Penetration testing is critical for organizations to proactively identify and address security vulnerabilities before they can be exploited by malicious actors. By leading penetration tests, organizations can uncover hidden security weaknesses, approve the viability of security controls, and prioritize remediation efforts to enhance overall security posture. It also helps organizations comply with regulatory requirements, protect sensitive data, and maintain customer trust and confidence in their security practices.
3. What Types of Penetration Testing Methods are Available?
Penetration testing strategies change depending on the extension, goals, and target environment. Normal sorts of this type of testing incorporate organization , web application , wireless , social engineering and mobile application penetration testing. Every strategy centers around assessing specific areas of vulnerability and reproducing different assault situations to identify security risks and weaknesses.
4. How Often Should Penetration Testing Be Conducted?
The recurrence of this testing depends on different factors, including the association’s risk profile, regulatory requirements, industry standards, and changes to the IT environment. As a rule, organizations ought to direct penetration testing consistently, for example, every year or semi-yearly, and at whatever point huge changes happen in the infrastructure, applications, or security controls. Continuous monitoring and intermittent testing assist with guaranteeing that security vulnerabilities are immediately identified and addressed to maintain a robust security posture.
5. What Are The Benefits of Outsourcing Penetration Testing Services?
Outsourcing penetration testing services to third-party security firms or ensured professionals offers a few benefits, including admittance to particular skills, high-level testing tools and methodologies, and fair-minded assessments of security posture. Outsourcing permits organizations to use the knowledge and experience of skilled security professionals, gain experience in rising threats and vulnerabilities, and get significant proposals for further developing security defenses.