Table of Contents
Software development security is a consistently developing worry for current software development. With the rise of cyber threats, companies should go to lengths to guarantee that their applications remain secure and protected from likely malicious activities. According to Forbes, more than 70% of organizations presently have some type of utilization security setup. Moreover, Harvard Business Review revealed that almost 50% of all data breaks happen because of insufficient security measures.
Numerous organizations will present present-day security instruments and arrangements to battle these security challenges. According to a review from Kaspersky, 75% of businesses have taken on some type of artificial intelligence (AI) or machine learning (ML) to distinguish and answer potential cyber threats. Also, over 50% of blockchain software development companies are utilizing advanced encryption technology to protect data in transit and very still.
These statistics demonstrate the severe security challenges present-day software development faces and organizations’ need to go to proactive lengths to protect their applications from malicious activities. By putting software development lifecycle security resources into advanced security arrangements, companies can more readily defend their clients’ data and guarantee that their applications remain secure.
Why is Software Development Security Essential to Modern Software Development?
Modern software development requires secure software, which is fundamental for protecting clients’ data as well as the respectability of the software. Software security guarantees that clients who are approved have admittance for microservices architectures to explicit capabilities or data and that criminals can’t take advantage of security shortcomings. Security for software development is a fundamental aspect of contemporary software development since it protects against data breaches, unapproved access, and other hurtful activities.
According to Forbes, cybercrime is a significant danger to the world economy, costing around 600 billion dollars annually. Harvard Business Review has reported that a more substantial number of companies were survivors of data breaches because of software that wasn’t secure. Software development lifecycle security is critical with the appearance of cell phones, distributed computing, and the Internet of Things.
With every one of the data being stored on servers that are remote and linked to physical devices, there’s an increase in the risk of security breaches by malicious attackers. Additionally, Forrester’s research found that 79% of companies think protecting their application development is their top security issue. In addition, Infosys reported that most businesses have invested in application security and software security, with an average investment of about $2 million every year. Secure software development lifecycle is clear evidence that security for software development is an essential aspect of every modern business.
Ready to Build? Let’s Create Your Software Solution Today!
What are the Cyber Threats and Potential Impacts on Software Development Security?
Cyber threats allude to malicious activities that utilize the internet or some other technology to hurt the security of a network, PC framework app, location, or data. Cyber-attacks can have different effects on the safety of software development. This part outlines the top cyber-related threats and their conceivable impact on software development security.
1. Malware
Malware can be depicted as any malicious software intended to eradicate or get to information and assets of the network or PC. Software security during development by conceivably compromising weak source code, causing issues to current applications, and surprisingly, taking client data.
2. Phishing
Phishing can be portrayed as a cyber assault that utilizes social testing strategies in software engineering to permit attackers who are malicious to gain admittance to individual information like passwords, usernames, account numbers, and other personal details. If practical, phishing assault might permit attackers admittance to delicate information and applications, which could represent a grave security peril.
3. SQL Injection Attacks
These SQL injection attacks can be depicted as a form of assault involving malicious code put into the application’s database in the expectation of gaining admittance to private data. It might bring about the theft of data from clients or modification of databases that are now in use, which prompts disturbances in the software development process.
4. Cross-site Scripting
Cross-site scripting (XSS) is a type of computer security vulnerability that allows an attacker to inject malicious code into web applications or websites. XSS vulnerabilities are a major concern for web developers, as they can be exploited by attackers in a variety of ways.
The severity of an XSS attack depends on the type of malicious code injected. In its most basic form, attackers may use XSS to inject client-side scripts into a page and steal information from unsuspecting visitors. For example, an attacker might inject a script that tracks users’ keystrokes or records their usernames and passwords when they log into a website.
XSS attacks might bring about clients’ data being taken or modified in a manner that isn’t authorized by the software development services in USA or malicious code running by a PC client.
5. Buffer Overflow Attacks
Buffer overflow attacks happen when malicious attackers send huge data bundles into online applications or administrations to make a buffer overflow. It can bring about an execution of unsafe software, loss of delicate information, or even the interruption of administrations.
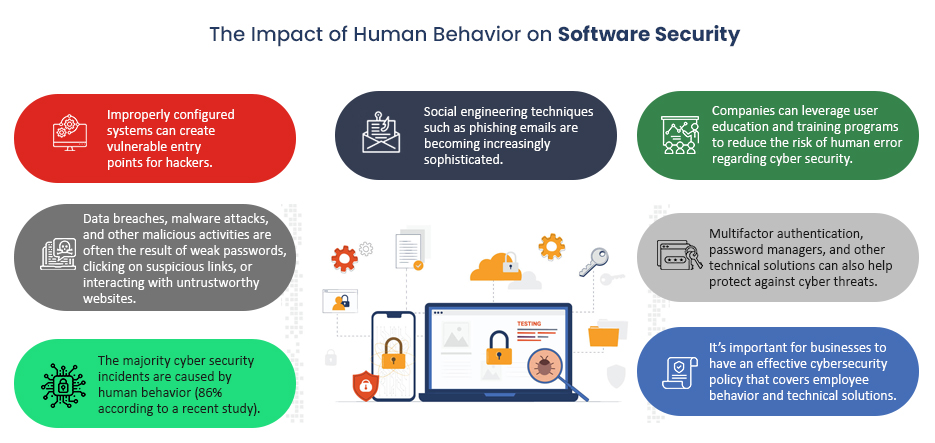
6. Social Engineering
Social engineering is one sort of assault that involves malicious actors who utilize mental manipulation and misdirection to gain admittance to delicate data. If they succeed, these attacks could bring about data theft from clients or interruption while developing software.
7. Man-in-the-Middle Attacks
Man-in-the-middle attacks are the point at which an assailant can get to an individual’s network association and intercept the traffic between two individuals. The attackers can then obtain secret information for fintech software development services, modify the data that is now in use, or introduce malicious code into the software.
8. DDoS Attacks
The distributed denial of service (DDoS) incident is an assault wherein malicious attackers send gigantic measures of traffic to an application to over-burden the framework, causing interruption of administrations. DDoS attacks might take significant personal time and interrupt the development of software processes in any custom software development company in USA.
Top 10 Software Development Security Challenges in 2025
Security for software development has grown to be more and more critical in today’s digital world. In the age of infected software, hackers, and cyber-attacks, it’s vital to ensure that developers are aware of and consider security threats when developing software programs. McKinsey & Company found that the average cost of fixing a software security vulnerability is $7,500.
Additionally, Infosys reported that the number of cyberattacks increased by 5% in 2020 compared to 2019, with malicious actors actively targeting vulnerable applications as an entry point into corporate systems. In this post, we’ll explore 10 of the most critical security issues software developers may face by 2025.
1. Cloud Security
If more organizations and companies transfer their information and apps onto cloud-based storage systems, cloud security will likely become an increasingly crucial issue for developers over the coming years. The software development lifecycle security systems should be protected from sensitive information from external threats but still allow authorized users easy access.
2. Artificial Intelligence
Since the field of artificial intelligence in software development advances the development of AI, developers must stay current regarding the newest AI technology and be aware of possible security issues. The developers must be mindful of the consequences of their AI models and ensure they’re built using robust security features to safeguard sensitive information from malicious hackers.
3. Automated Security Testing
The increasing complexity of software makes it challenging for developers to manually test their apps’ security to identify potential concerns. Security testing tools that automate the process allow developers to quickly detect the security weaknesses in their applications before they become vulnerable to external threats.
4. Mobile Security
As organizations and custom enterprise software development migrate to mobile-based platforms, mobile security will likely become a critical concern for programmers.
5. Data Protection
Data security is a significant issue for developers to consider shortly as hackers seek out organizations’ confidential information. Developers should be sure that their applications include security mechanisms for authentication in custom software development for startups and encryption to safeguard sensitive information against outside threats.
6. IoT Security
The growing acceptance of the Internet of Things (IoT) has resulted in a requirement for safer gadgets and applications. As the number of users of these devices rises, so does the security risk posed by malicious actors. It is up to developers to ensure that they are aware of the security threats associated with these devices and take steps to protect user data from unauthorized access.
Developers should also be familiar with serverless computing, a technology that allows for the development of custom software without having to manage server hardware and software. This technology is especially useful for mobile apps, as it eliminates the need for physical servers and reduces the cost associated with managing them.
7. Application Security
Application security is one of the major concerns for developers in the future since malicious actors are continuing to attack vulnerable software. Developers should be sure that their applications have security mechanisms for authentication and encryption to shield user data against outside threats.
8. Network Security
Network security is an essential element of any software program that is secure. Developers need to be aware of the threats posed by network security and ensure that their software development security applications have solid security measures that protect the user’s data from malicious attackers.
9. Cryptocurrency Security
Cryptocurrency has become increasingly popular, and as a result, it has become an attractive target for hackers and scammers. Developers should prioritize implementing strong security measures to reduce the risk of cyber attacks or data breaches.
To start, developers should make use of secure coding practices and frameworks. Secure coding practices are essential to building applications that are resistant to attacks. This includes proper authentication and authorization, input validation, encryption, and data storage strategies.
Software development services in USA must be aware of cryptocurrency’s dangers and ensure that their apps are safe enough to protect sensitive data from external threats.
10. Identity and Access Management
In today’s world, software security is more important than ever. With the proliferation of mobile devices and cloud-based services, user data is increasingly vulnerable to attack by malicious players. As such, developers must design secure authorization and authentication mechanisms for their apps to protect user data from these threats.
Secure authorization and authentication mechanisms involve implementing systems that verify a user’s identity before granting access to protected resources. These systems must be able to identify legitimate users and differentiate them from potential attackers. Additionally, secure authorization and authentication mechanisms must also make sure that data is only accessed by authorized personnel.
Innovate, Automate, and Excel with A3logics Custom Software Development Services
What are the Best Practices to Identify Data Breach Vulnerabilities?
Security breaches have become more regular in recent times. In 2023, the globe witnessed the highest number of data breaches, leaving more than 7.9 billion records being compromised. This means that organizations must take action to ensure their security and detect any vulnerabilities that could result in an attack. This section will summarize guidelines to identify potential data breach weaknesses. Therefore, the top 10 security issues in contemporary software development by 2025.
Best Practices to Identify Data Breach Vulnerabilities:
1. Perform Regular Security Audits
This audit should examine all aspects of software development security. moreover, such as code practices, system architecture, and policies for accessing users, ways to authenticate users, etc.
2. Implement Security Policies and Processes
Companies should establish a framework of security guidelines and procedures to reduce the likelihood of security breaches. Software development security includes:
- Setting up user access control.
- Establishing security guidelines for coding.
- Using security programs for patch management.
- Frequently update your system’s security settings.
3. Use Secure Development Lifecycle (SDL)
SDL is a proven way to ensure the security of software. SDL is a method of providing safety for software. The secure software development lifecycle comprises several phases, including development, design and testing, integration, and deployment. Every stage must include strict security checks and tests to ensure the system is secure.
4. Use Automated Security Testing Tools
Automated security tools can assist in identifying potential vulnerabilities within the system. The devices can scan for vulnerabilities known to be vulnerable and create reports that outline improvements.
5. Monitor System Activity
The organization should be aware of its system for suspicious activity, like questionable user access or other internet traffic. Regular monitoring can help companies recognize security risks and act swiftly.
6. Implement Encryption for Data Storage and Transmission
The encryption tool is an effective method to protect data from unauthorized access. Blockchain software development companies should secure their data at rest and data moving through the network to ensure that only authorized individuals have access to sensitive data.
What Secure Coding practices should developers be conscious of?
Security-conscious code techniques are a fundamental part of the development cycle. They will help ensure the software is secure and protected from malicious assault. The most common way of creating secure code is a combination of skill and information. Still, there are some essential code-writing practices that software development security designers should be conscious of. Understanding software development lifecycle security through these accepted procedures is fundamental to composing secure code and safeguarding clients against security risks.
1. Input Validation
Input validation is a process that validates and confirms user inputs in software applications. This helps ensure that data input by the user is accurate, precise, and in line with the information the program anticipates receiving.
2. Error and Exception Handling
Handling errors and exceptions is a crucial security-conscious coding method that allows for identifying and repairing application bugs. Ensuring your application will continue functioning correctly when unanticipated situations happen is essential. In the event of an error or exception, it lets developers stay clear of errors, crashes, and security flaws.
3. Security Logging
Security logs are another essential safe coding technique. Developers can observe and track events in the application, like user activities or errors, alerts, and other system details. Software development security logs can assist in identifying possible exploits or suspicious activities for custom software development companies in USA that could be taking place within the application.
4. Secure Authentication and Authorization
Security is the most important aspect of any application, regardless of its purpose. Authorization and authentication are two key components that must be in place to ensure that only authorized users can access the application and its resources. Authentication is the process of verifying the user’s identity.
5. Data Encryption
As cyber-attacks become increasingly sophisticated and data breaches occur more frequently, organizations must take measures to protect sensitive information. One way to secure confidential data is by using encryption technology. This is one of the most effective ways to secure confidential information and keep it safe from malicious attackers.
In addition to encryption technology, serverless computing is another great way to protect sensitive data. Serverless computing refers to an application architecture that allows users to run code without having to manage or maintain the underlying servers. With this technology, organizations can focus on building and running applications. While leaving the hosting and security to a third-party provider.
6. Access Control Lists (ACLs)
A list of access control (ACL) is an essential method of coding that is secure. It helps ensure that only authorized individuals can modify and access the data. ACLs permit developers to define the users and processes allowed to read, write, or carry out specific tasks.
7. Security Testing
Security testing is an integral element of developing secure software. It assists in identifying possible software development security weaknesses and evaluating the security overall of the software. This includes design, programming, and deployment.
8. Secure Data Storage
Secure storage of data is an essential practice of secure code, which protects data from unauthorized access. A properly configured solution for data storage is a great way to ensure that only authorized individuals can access sensitive data.
9. Secure Network Communication
Network security is essential to safeguard data from unauthorized access. Developers need to ensure that all communications between their applications and the other systems are secure and protected with authentication. In addition, developers must use safe protocols like Transport Layer Security (TLS) to safeguard data while it is transported for software development security.
10. Application Hardening
The purpose of application hardening is to minimize the number of features, functions, and capabilities that can be exploited by an attacker. By reducing the attack surface, an application is less likely to be vulnerable to attack. As well as more resilient against malicious activity.
Application hardening can also involve using various technologies to protect the security of an application. These technologies include encryption techniques, authentication methods, authentication protocols, access controls, user authorization mechanisms, and application firewalls.
This helps decrease the possibility of vulnerability attacks and malicious attacks against the application.
Empower Your Business with Cutting-Edge Software. Request a Free Consultation Today!
What are the advantages of Integration Security practices within DevOps?
In this segment, we will examine the benefits of integrating security measures into DevOps, emphasizing how it further develops efficiency, how custom software development outsourcing helps set aside time and money, and how it further develops trust and fulfillment among clients.
1. Improved Efficiency
By integrating security into the DevOps strategy, engineers can rapidly recognize any shortcomings before implementing applications. This permits them to fix the issues more quickly and avoid costly deferrals or errors.
2. Reduced Costs
By integrating security into the DevOps strategy, organizations will want to decrease the cost of security reviews, testing, and inspection. The expense of remediating weaknesses that could be available. This will assist with increasing the worth of the financial plan for software development.
3. Improved Compliance
Security in DevOps guarantees that applications follow the necessities of regulatory offices like PCI-DSS or HIPAA. This can assist with protecting clients’ very own information and ensure that companies comply with the material regulations.
4. Increased Trust
In proactively integrating security into the DevOps procedure, blockchain software development companies can show their clients that they genuinely esteem your security concerns. This further develops certainty and fulfillment of the client, which is fundamental for ensuring long-haul accomplishment.
5. Improved Quality Assurance
Security measures carried out in DevOps aid developers in identifying potential weaknesses and bugs before they’re sent. Which diminishes the expense of patching and debugging after creation.
6. Improved Agility
Organizations can send minor changes or updates in minutes by securing applications during the development stage. This can assist with improving their efficiency and staying in front of the opposition in software development security.
What are the Best Cloud Security Considerations for Secure Software Development?
Secure software development in cloud platforms can be complicated to attain. However, it’s essential to ensure the security and protection of confidential data. To ensure that cloud-based systems for software are safe, software development security needs to be considered. A few critical considerations when creating and deploying apps.
1. Authentication
It is essential to authenticate all users who use an application and any other third-party applications or devices. The authentication process should use secure methods like multi-factor authentication.
2. Authorization
Allow access to apps and other resources based on roles-based permissions. This ensures that only users can access the information and resources they require.
3. Encryption
Any sensitive information must be secured at rest and during transport to shield against unauthorized access.
4. Data Validation
It is fundamental to check client information and input before the data is stored in a database or imparted to other projects. Software development lifecycle security guarantees that programmers can’t insert malicious code into an application and that there is no break in software development security.
5. Access Control
Organizations should involve access control records to restrict access to specific assets like databases and reports. It is prescribed to give access based on the need to be aware.
6. Firewalls
Businesses should use firewalls to shield their networks from programmers and protect their applications from threats. The firewall should be intended to allow just known traffic and is routinely checked to guarantee that software development security approaches are not changed.
7. Security Testing
The organizations should periodically test their application’s security with static, dynamic, and penetration test methods. This ensures that vulnerabilities in security are discovered and fixed before hackers can use them.
8. Disaster Recovery Planning
Companies need a disaster-recovery plan specifying how an organization can respond to cyber-attacks, data breaches, and other security risks. It should include methods for recovering software and systems should there be a cyber-attack.
9. Security Audits
Security audits for custom software development services are a must for all organizations. They check to verify the security of their systems and comply with industry standards and rules.
10. Security Education
The Company should educate its employees on security best practices and ensure they know the most recent security threats. This helps ensure employees are equipped to recognize potential risks and take appropriate action.
Looking for a Tech Upgrade? Let’s Build Your Next Software Solution Together!
How do Emerging Technologies Impact Software Security Development?
The explosive growth of contemporary technology has resulted in the demand for more developing software security. With the advancement of technology, so does the possibility of malware-based attacks against computer systems. New technologies are continually developing and being released to the marketplace. So developers of software development security must remain ahead of the game by recognizing how emerging technologies will impact security software development.
1. Cyber Threats and Potential Impacts
Cybercriminals constantly seek methods to take advantage of technologies and software. Developers must be aware of the latest cyber-security threats and their potential impact on the security of their applications.
2. Best Practices to Identify Data Breach Vulnerabilities
Making sure you have adequate security measures and monitoring tools is essential in detecting vulnerabilities to data breaches before being used. Custom software development outsourcing is recommended that developers follow best practices for ensuring input is valid, encrypting sensitive information, and using secured authentication protocols.
3. Secure Coding Practices That Developers Should Be Aware Of!
Security-conscious code practices are crucial to protect software development security programs against malicious attacks. Software developers should keep up-to-date on current secure code best techniques, including validating inputs output encoding access control.
4. Benefits of Integration Security Practices Within DevOps
Integrating security-related processes into the development process will help detect security threats before they become an issue. For software development project management can improve cooperation between the developers and IT experts, improve code security, and enhance app performance.
5. Best Cloud Security Considerations for Secure Software Development
Cloud computing has become widely used to manage and store information. It is vital to employ safe protocols, such as SSL/TLS multi-factor authentication (MFA) encryption while using cloud-based solutions to develop software.
6. Emerging Technologies and Their Impact on Software Security Development
With the advancement of technology, new techniques continue to evolve. These technologies can provide benefits and risks to security software development. It is crucial to consider the possible impacts of new technologies like blockchain technology, artificial intelligence, and quantum computing when developing safe software systems.
What are the steps to choose the most suitable software development firm for your venture?
Selecting the right software development firm to work with is essential to ensure your venture succeeds. Understanding that the software development security industry must be equal is crucial. It’s critical to study potential companies before making a final decision. According to a report by MarketsAndMarkets, the global data security market size was valued at USD 51.51 Billion in 2019 and is expected to reach USD 125.31 Billion by 2025, registering a CAGR of 14.6%. In this post, we’ll discuss several important factors to consider when looking at companies for software development.
1. Experience and Expertise
Choosing a custom enterprise software developer with the relevant skills and knowledge is essential to create the software you’re looking for. Request references or look at previous work they’ve completed because this can reveal their team’s capabilities.
2. Technical Capabilities
The business should possess the necessary technical skills for developing your application. Including experience with programming languages and frameworks and knowledge of databases.
3. Quality Assurance
Check that the firm you select has a reliable quality assurance system in place since this is vital in developing quality software. Be aware of their bug-tracking procedures, peer reviews, code guidelines, etc.
4. Cost-Effectiveness
You must ensure you get the highest return on the software development you plan to do. Check out the price system and the additional services they might provide.
5. Support Services
A good customer support service is crucial to any software development lifecycle security venture. Make sure that your company choice has good customer support service.
6. Communication
Communication is crucial for any software development venture to succeed. Learn how your Company interacts with its clients via telephone calls, emails, or video conferences. Check if they have an assigned project manager to ensure effective communication.
Transform Your Software Vision into Reality – Book A 30 Minutes Free Consultation!
Conclusion
The modern software development process presents a variety of security issues. As the complexity of both networks and systems increases, developers must be able to take proactive measures to ensure their apps are safe. A combination of security-conscious code methods, vulnerability testing, security modeling, and code review. Continuous monitoring accomplishes a secure software development lifecycle.
Secure Coding practices use input validation and sanitization methods to stop malicious code from getting infected into applications. Testing for vulnerability should be performed frequently to detect any vulnerabilities that could result in the possibility of a breach. Ensuring that every software complies with security’s best standards is equally important.
Threat modeling is the process of analyzing possible risks and examining the system’s structure to determine if it can withstand the risks. IBM found that the average data breach cost was $3.9 million in 2019, an increase of 15% from 2018. Forrester also found that 25% of organizations have experienced a data breach caused by insecure software development practices. Gartner reported that 64% of organizations invest in application software development security solutions to protect their applications proactively.
Frequently Asked Questions!
1. How do you tackle Software Development Security Challenges Modern Software Development faces?
Modern Software Development Security faces numerous security issues, including application layer attacks, systems layer attacks, database layer attacks, and attacks on network layers. Other security threats are data theft or loss. Access control systems that are not secure, insecure programming practices, and malicious insider activities.
2. What can I do to protect my software development processes?
It is possible to secure the development of your software with the help of a few good techniques. This includes regularly performing security testing, code review, threat modeling, and continuous monitoring. Additionally, you should employ safe coding practices to stop introducing malicious code into your application. Further, it would help to consider using emerging technologies such as AI, ML, and blockchain to enhance security.
3. What are the advantages of using security techniques in DevOps?
DevOps is a software engineering testing strategy that combines operations and development to reduce the time it takes to develop. By integrating security techniques in DevOps, companies can ensure that their apps are safe and secure from the threat of malicious actors. Integration of security practices can help enhance the communication between operations. Developers teams when they work together when releasing new versions of applications.
4. Are cloud security issues essential to know while designing software?
When developing software on cloud platforms, programmers must be aware of security best practices, like employing multi-factor authentication, and encryption of information at rest. While in transit, constantly monitoring access logs, and roles-based access control. Furthermore, developers need to ensure that their apps are secured when connecting to external platforms or services.
5. What can I do to protect my program from hackers?
Your software can be protected against malicious hackers by adopting security-conscious coding practices, and periodic vulnerability tests. That is a threat modeling method. Also, think about the possibility of using emerging technologies like AI, ML, and blockchain technology. To recognize malicious activity and ensure your data’s integrity. Make sure your apps are securely connected to other systems or services.
6. What is the impact of having insecure practices for software development?
Failure to adopt safe software development practices by many software development services in the USA may have severe consequences for any organization. Without these best practices, businesses could be at risk of hacking, data loss, and identity theft. In addition, it may result in reputational damage when customers’ data is stolen or applications stop functioning because of a security problem.






